Banking these days has become electronic in nature. E-banking, swift, money transfer, internet banking, ATM, just to name a few, are all electronic in nature. This phenomenon has made it necessary for most banks to “re-tool”, changing their network systems to conform to current trends in banking, thinking of cost as well.
Most banks are now considering saving their data in the cloud. This definitely saves cost, but creates headaches for central banks’ supervision and inspection teams. The major problem with this idea is jurisdictional limitations when it comes to legal request for data during investigation. As data is being stored offsite, there will be a little the central bank can do to unravel instances of financial malfeasance should there be one. The idea of data being stored offsite could also aid banks to launder money without being caught.
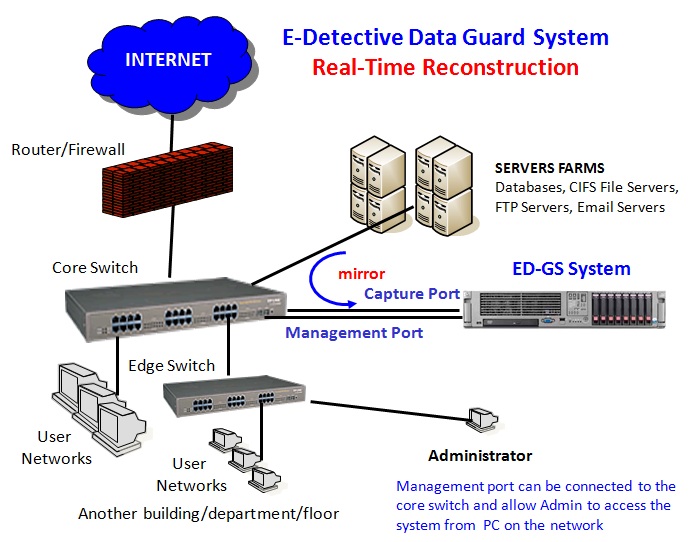
To keep monitoring banks that store data offsite, there is the need for central banks to drum up a policy that will mandate every financial institution to setup E-detective Data Guard system; what I call the “Black-box for financial investigation”, at the core of its data center. This black-box, will record every data packet traversing the banks network to the cloud. The recorded data captured will be sitting at the bank’s data center, which can be accessed by the banking supervision team at any time without any problems. I can foresee complaints from the banks about privacy, which should not be an issue with this solution because it is a “black-box”, meaning data can be accessed only when there is the need, with the right requests, procedures, and authority.
The process:
A: The Head of Banking supervision initiates inspection process based on; complaint, suspicion, or annual review.
B: A bank Inspector is authorized to access “Black-box” with exact specifics for data to be collected, by being given an authorization code to access Central Management System (CMS).
C: Bank Inspector accesses “black-box” to retrieve data of interest. (Within search limitation”)
D The data is analyzed and report written to Head of Banking supervision team for action to be taken
E: Based on results generated, bank under investigation gets written to for response.
This process will be fair, transparent and straight forward. It will confirm to compliance to Basell III, Sarbanes-Oxley, ISO/IEC15408, PCI and other standards set for banking institutions. I believe central banks worldwide will consider this black-box concept. |